
SD-Entry Style Revisited: Internet Border Complex
[ad_1]
I just lately posted a site about the prior blogs I’d penned about SD-Accessibility/DNA Heart style and some implementation specifics. My intent there and in this weblog is to update y’all with some far more the latest discussions I and some others have been getting.
Much more just lately, I/we also posted an update about SD-Accessibility (“SDA”) Sites.
A single other matter looks to preserve coming up, both in an SDA context and in a general context: the World-wide-web connection, which all people seems to do differently. And at times badly if the intent is Large Availability (“HA”). Probably we ought to simply call it “The Kluge Zone” (with eerie audio accompanying it).
For SDA, this can be a deep style and design subject matter if you’re utilizing SDA Transit.
Solitary exit is quite uncomplicated. It has to be. LISP will present what quantities to a default route indicating, in impact, “to leave SD-Obtain land, tunnel traffic to this Border Node (or HA pair).” That tunnel usually terminates in the knowledge centre in fairly close proximity to your World-wide-web exit route. If your knowledge middle has other things (like a web-site or two) involving it and the Internet exit, that might have to have extra thought. That condition tends to be rare (or I’d like to consider so). And the things to consider described under nonetheless utilize. With SDA Transit, you still get to decide a person or additional default exits, which may be your Net blocks or your data middle blocks, but it cannot be both of those.
When you have two web pages offering Online exit, points get far more tough. If you want failover, there are some basic but non-evident approaches to develop it.
A element I’d long awaited from Cisco called “border prioritization” was created but reportedly has been buggy for a though. The thought (as I recognized it) was to be equipped to specify the border site you want for Web egress, with failover to the other web page. The previous I read was operate is getting carried out to deal with that and that a characteristic known as regional about-journey may well be coming sooner that could possibly be pertinent. Each attributes do not occur up in Google or Cisco lookup, presumably since not formally supported nonetheless. You will will need to communicate to Cisco SDA gurus if both of these capabilities audio fascinating or required for your design. I’m surely in no position to chat about interior Cisco perform in progress.
Late update: Cisco HAS been speaking, e.g. at Amsterdam, about a precedence aspect: consider over-all primary and fallback exits.
Due to the fact this was first drafted, I’ve identified out about a model-new Cisco function for SDA known as “Affinity”. It was apparently declared in Oct 2022 and was evidently too new for CiscoLive Amsterdam. I’ll write-up a individual weblog about it as a stick to-on to this 1. If this is urgent for you, converse to your Cisco TME.
So, what can you do with perfectly-recognized and acquainted, trustworthy technology?
How Do I Aid Dual Exits?
All is not misplaced!
With a modicum of superior-pace interconnection, you can get a considerable diploma of multi-internet site significant availability reasonably simply just.
The most straightforward solution is arguably to operate IP Transit. AKA “VRF-Lite on all underlay links”. Not way too negative if you have only 2-4 VNs/VRFs. Messy if you have more.
What that purchases you is the skill to select which prefixes and metrics to use to immediate website traffic to in which you want it. I like BGP for that, myself. Connection state protocols like OSPF and IS-IS make targeted visitors engineering a bit more durable.
Dual Exit Diagram
In this article is a new, improved edition of a diagram I’ve utilised prior to, built in particular to go over this circumstance.
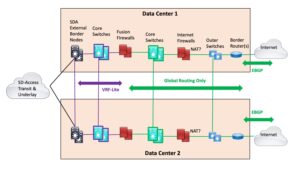 Notice: I drew solitary strains to decrease clutter. In actuality, the vertical pairs at the two sites would be connected by two or 4 cross-links (“rectangle or bowtie”). For that make any difference, the horizontal back links (strains in the diagram) would also be two or 4 backlinks.
Notice: I drew solitary strains to decrease clutter. In actuality, the vertical pairs at the two sites would be connected by two or 4 cross-links (“rectangle or bowtie”). For that make any difference, the horizontal back links (strains in the diagram) would also be two or 4 backlinks.
The plan is to run SDA Transit into two pairs of “External Border Nodes”. Just one pair in each and every of the two data centers: demonstrated on the still left previously mentioned. The purple highlights exactly where VRF-Lite is managing (or “IP transit” – I steer clear of that term for this localized scenario since it appears to include unneeded obscurity). The VRF-Lite operates into the still left aspect of the Fusion Firewalls (“FFWs”). Every thing in the FFWs and to their correct is world wide routing only.
The purple core switches are just VRFs on the exact same bodily switches that are shown with inexperienced highlights. Or they can be independent switches if that helps make you feel improved, you want simplicity, or you like contributing to Cisco’s base line.
I attract the diagram this way considering the fact that everything else I’ve tried finishes up with triangles in it or just appears to be like unusual. (E.g., stacking the purple and eco-friendly core switches in the diagram.)
Why do it this way?
Well, the crucial level is that it de-couples the SDA network from the firewalls and edge. Fundamentally, SDA Transit will get your targeted visitors to one particular of the information facilities, and if there is a firewall issue, you can shunt the targeted visitors to the other data middle, and back if vital/ideal.
The design and style concern at engage in in this article is maintaining firewall state for flows and return site visitors. Especially extended-lived flows.
For this style, I would run BGP on the FFWs, so that if there is a dilemma, routing on the two left and appropriate sides will change stateful traffic to the other internet site. (Information still left to the reader.)
You then have the option of jogging with a favored web site or not. Because the FFWs can involve a great deal of potential, they may possibly be high-priced, which will develop the urge to use them. If you select to do that, you have all the usual routing tools to do the job with, somewhat than possessing to rely on SDA functions that might not exist or are new and perhaps buggy.
LISP Pub/Sub
My knowledge is that SDA LISP Pub/Sub at current gives you the means to designate World wide web exits, and round-robins if there are many such internet sites.
The previously mentioned style with its decoupling allows you have dual web page HA and “fix” the routing to do what you feel you need. Solitary favored exit for simplicity, or twin with a lot more complexity.
About the FFWs
It seems like I should really consist of a reminder about what the FFWs are there for.
Their main intent is to handle traffic going concerning VNs/VRFs. That’s presumably why you developed the VRFs in the initially place: you wanted to isolate friends, IOT, PCI targeted visitors, whatever.
The next reason is as 1 probable position to handle person to server access, a common need to have unless you’re maybe carrying out ACLs in some variety in VMware NSX. Or much less generally, ACI. That’s also almost certainly how you filter server to server flows.
Frequently, web-sites I have found now have an outside the house firewall pair, managing server to Internet site visitors, and generally person to World wide web as well.
Failure Modes
Assuming reasonable routing, and many others., a single gadget failure or one url failure should not be a difficulty. There’s a Ton of redundancy there!
Let us examine some failure modes.
- External border pair failure or minimize off from underlay at one web page.
IP Transit or LISP Failover would be necessary. IP Transit would be your common IGP or BGP failover.
LISP with no Pub/Sub appeared to NOT fail more than, or at the very least only quite little by little, the last time I analyzed it. LISP Pub/Sub is new given that the previous time I had the opportunity to do testing.
- Border pair to FFW, FFW, or FFW to core switches failure.
With dynamic routing (with the FFW taking part), website traffic ought to go by using the other info middle. If you have a desired exit via the Net at the data centre with the failure(s), traffic should go back again across the crosslink, etcetera. (Sub-exceptional, but beats enjoying games with, or ready for World-wide-web failover?)
And if you look carefully, the entire FFW block story results in being the identical as the core swap/World-wide-web firewalls/outer switches (or routers) story, as far as routing and failover.
In limited, this technique de-couples how the packets get to one particular of the knowledge centers (IP Transit or LISP-based mostly SDA Transit) from the entire firewalling and World-wide-web routing problem. Which is a good matter. Modular style, lowered complexity.
But!
Take note that the above assumes the two exits are rather nearby, so that latency is a non-concern. If they are considerably apart, then you will probably want place-conscious exit priorities, which is a summary of what Affinity can do.
What I can not conveniently explain to you how to do is attain load-sharing throughout exit complexes. The problem to load-sharing is preserving firewall state. Coverage routing centered on resource IP block would seem like it might be turned into a workable remedy.
If you’re inclined to do cross-web-site firewall clustering, then stateful return paths is no huge issue. I’m video game for localized firewall clustering, but cross-web site clustering strikes me as including complexity and chance (new failure modes) fairly than escalating availability.
Yeah, it would allow for use of the secondary website units and back links, neither of which is probable low-cost.
Drawback: if the cross-hyperlinks fall short concerning internet sites, you nonetheless have a dilemma. Put differently, adding cross-web-site failover to a routing plan that employs equally Net exits statefully adds an additional increment of complexity. Do you truly want to go there?
Late Take note: Affinity looks to support handle this!
Variations on This Theme
Static routes – just say no.
If you use general public addressing internally and do NAT on the firewalls, to two different general public blocks that are externally advertised (i.e. 2 x /24 at a minimum), then that perhaps simplifies condition preservation. Promoting a /23 and one of the /24s out of each web site might be useful in that circumstance.
I do not have any other concepts at the moment. Specially kinds that prevent complexity.
Need to have More Control?
It’s fewer classy, and possibly a lot more configuration perform, but IP Transit could be a really serious consideration below. Specifically if you don’t expect to have a lot more than a few of VNs (VRFs) in your SD-Obtain network. (Be positive, due to the fact afterwards on switching from IP Transit to SDA Transit would seem like it would be unpleasant?)
What that purchases you is a larger set of routing instruments for which visitors goes wherever.
Summary
I hope this receives you imagining about your World wide web exits and redundancy, and what your failover tactic is.
I have viewed a lot of designs in which Net twin-web site automatic failover has not been carried out, or only is effective for some failure modes. Also, I and others used to not rely on dynamic routing on firewalls (or not believe in the firewall admins), possibly because of to unpleasant CheckPoint ordeals. But all that may have modified without us noticing!
Many thanks to David Yarashus and Mike Kelsen (and J.T.) for discussions and insights about this subject matter.
[ad_2]
Resource link





